What is the need of xor-ing the key with an outer and inner pad in HMAC? - Cryptography Stack Exchange
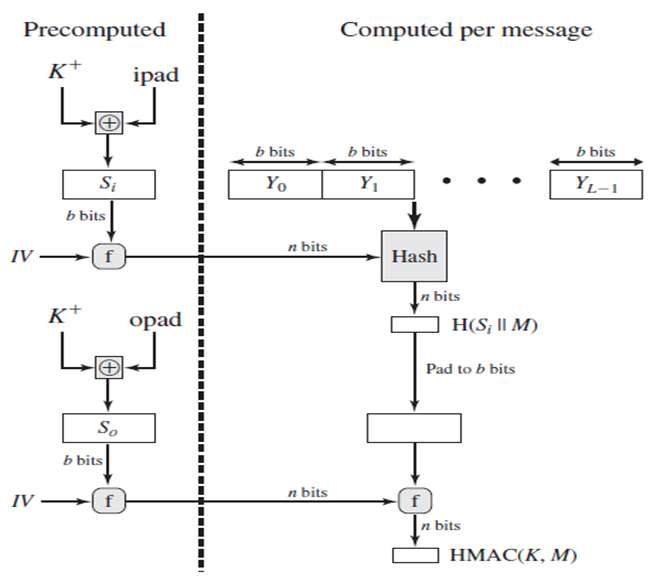
Chirag's Blog: HMAC | MAC based on Hash Function | HMAC Structure | HMAC Impelmentation | HMAC Pros & Cons
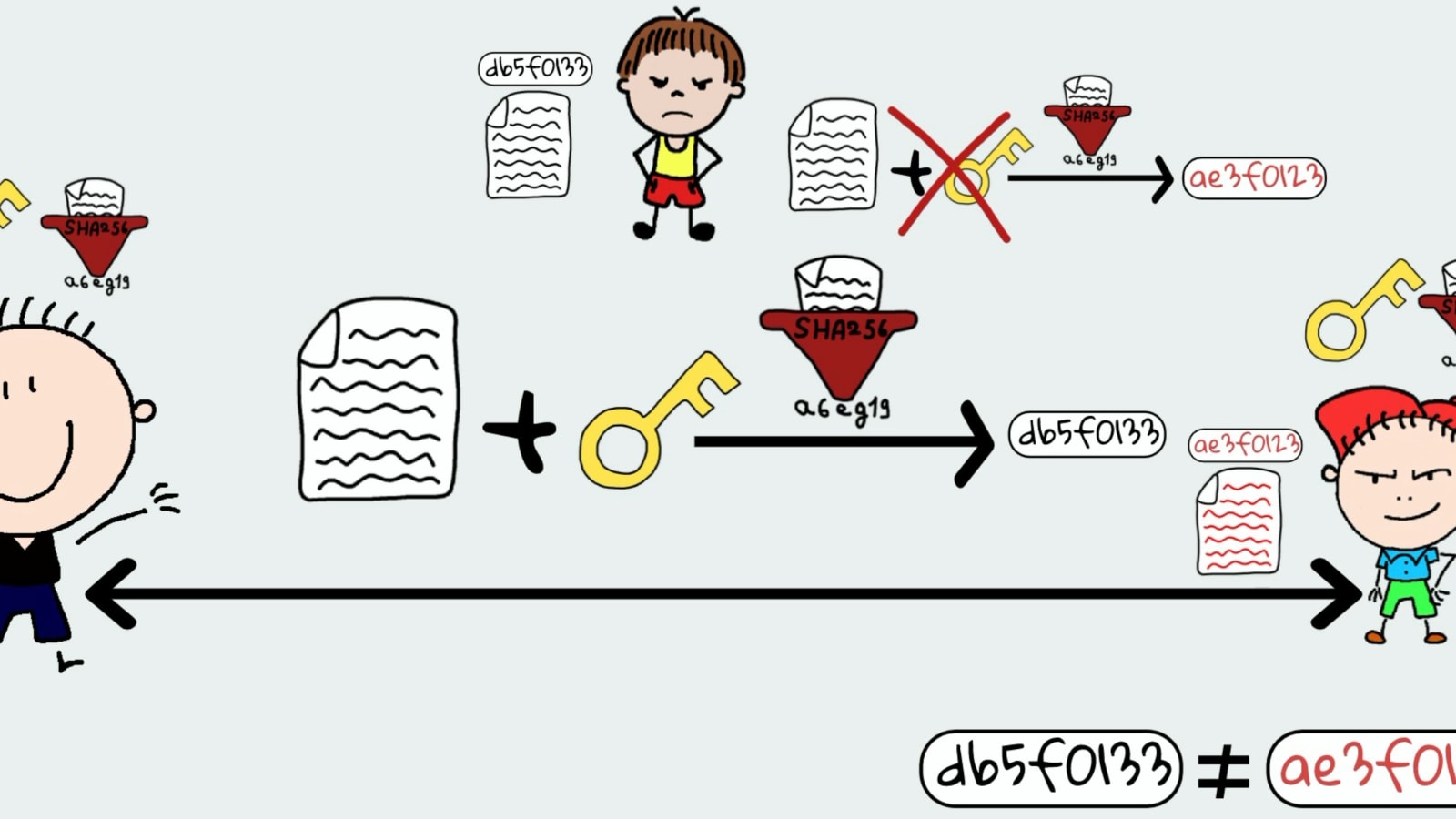
HMAC & Message Authentication Codes - Why hashing alone is NOT ENOUGH for Data Integrity - DEV Community

HMAC & Message Authentication Codes - Why hashing alone is NOT ENOUGH for Data Integrity 😼 - DEV Community

HMAC - Lecture materials - HMAC Hash-based Message Authentication Code Developed by Mihir - Studocu

Hash Message Authentication Code (HMAC) process. 3.3.2. Overview of... | Download Scientific Diagram

Basic HMAC generation For a recap, in Fig. 1, HASH stands for the hash... | Download Scientific Diagram

HMAC Construction HMAC uses the following parameters: H = hash function... | Download Scientific Diagram

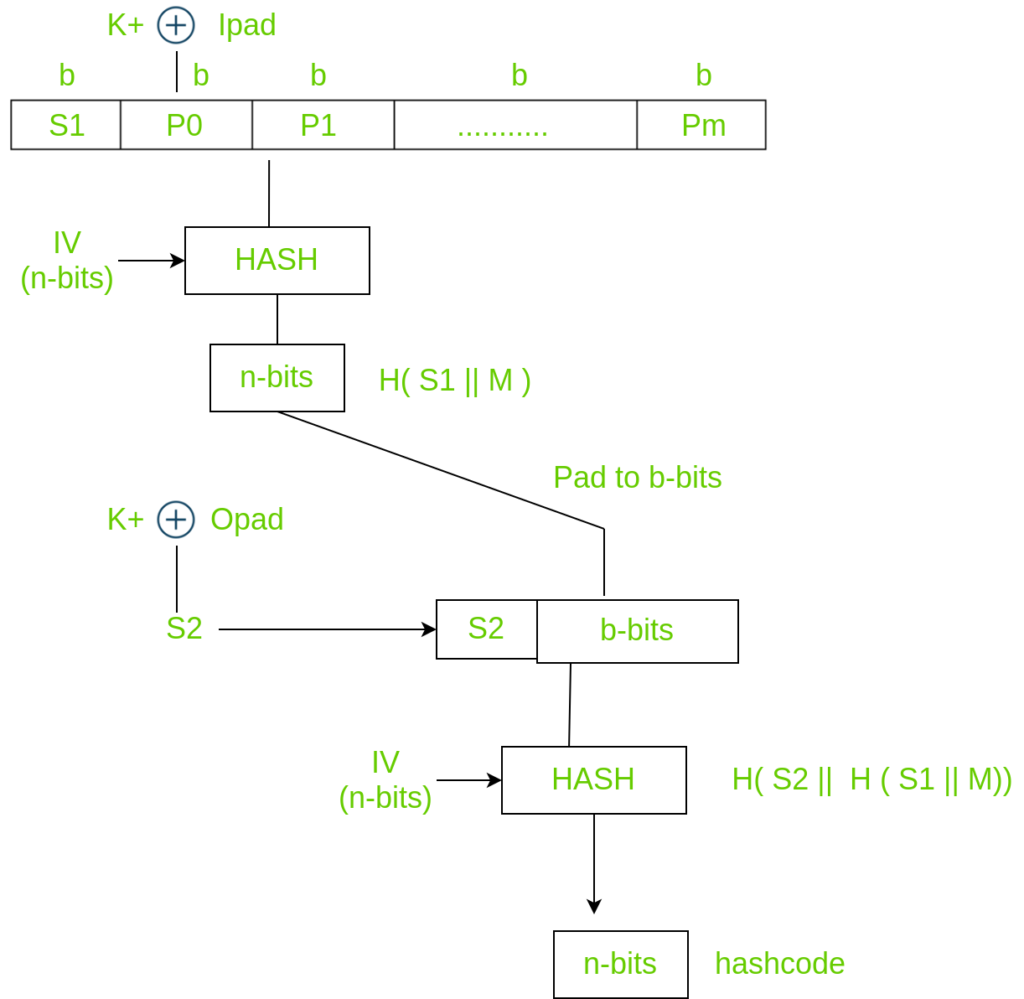
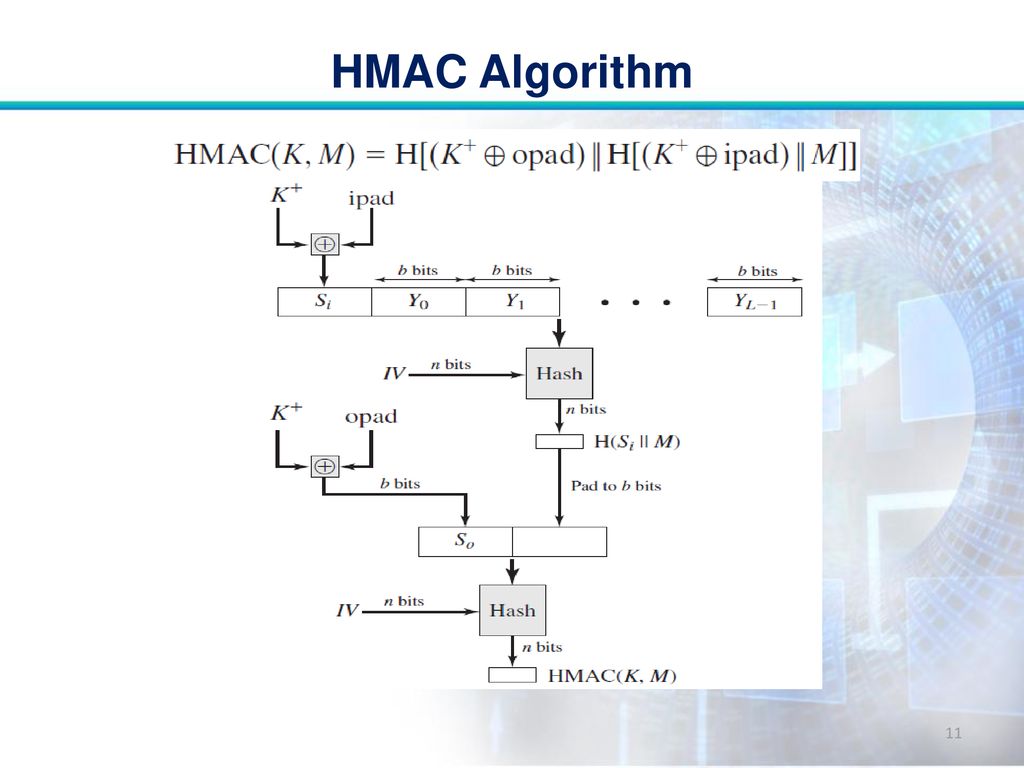
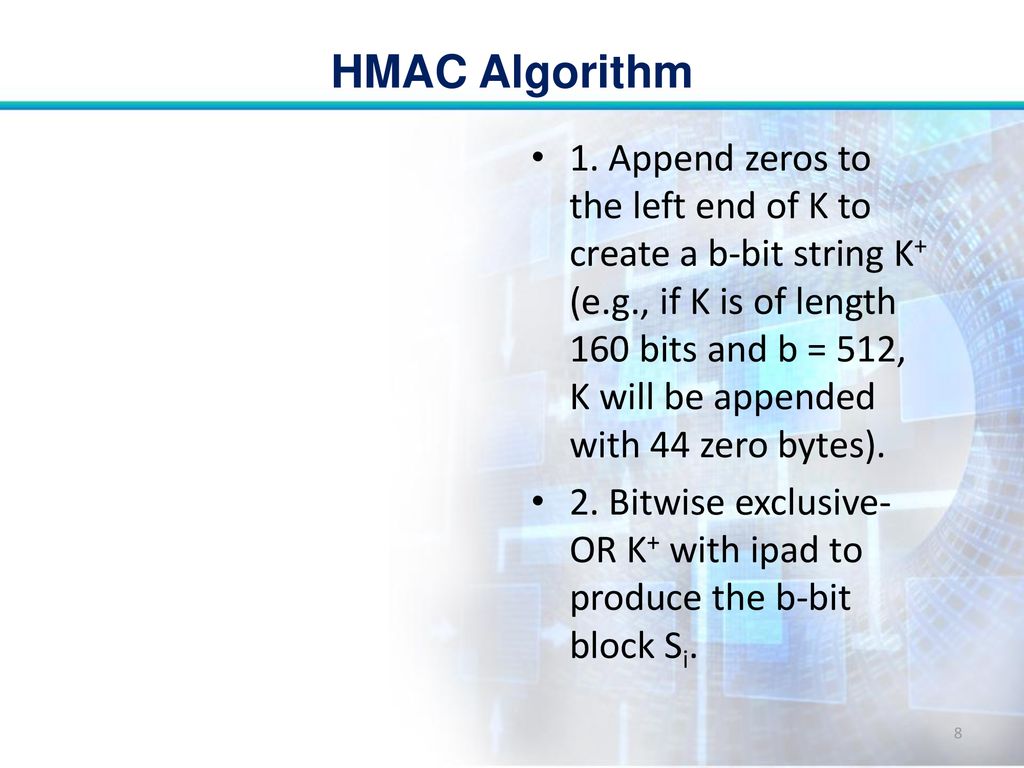
SOLVED: Please explain this picture. K+ iPad b bits b bits Y1 b bits YL-1 Si Yo HMAC n bits IV Hash opad bits HSIM K Structure b bits pad to b

Chirag's Blog: HMAC | MAC based on Hash Function | HMAC Structure | HMAC Impelmentation | HMAC Pros & Cons


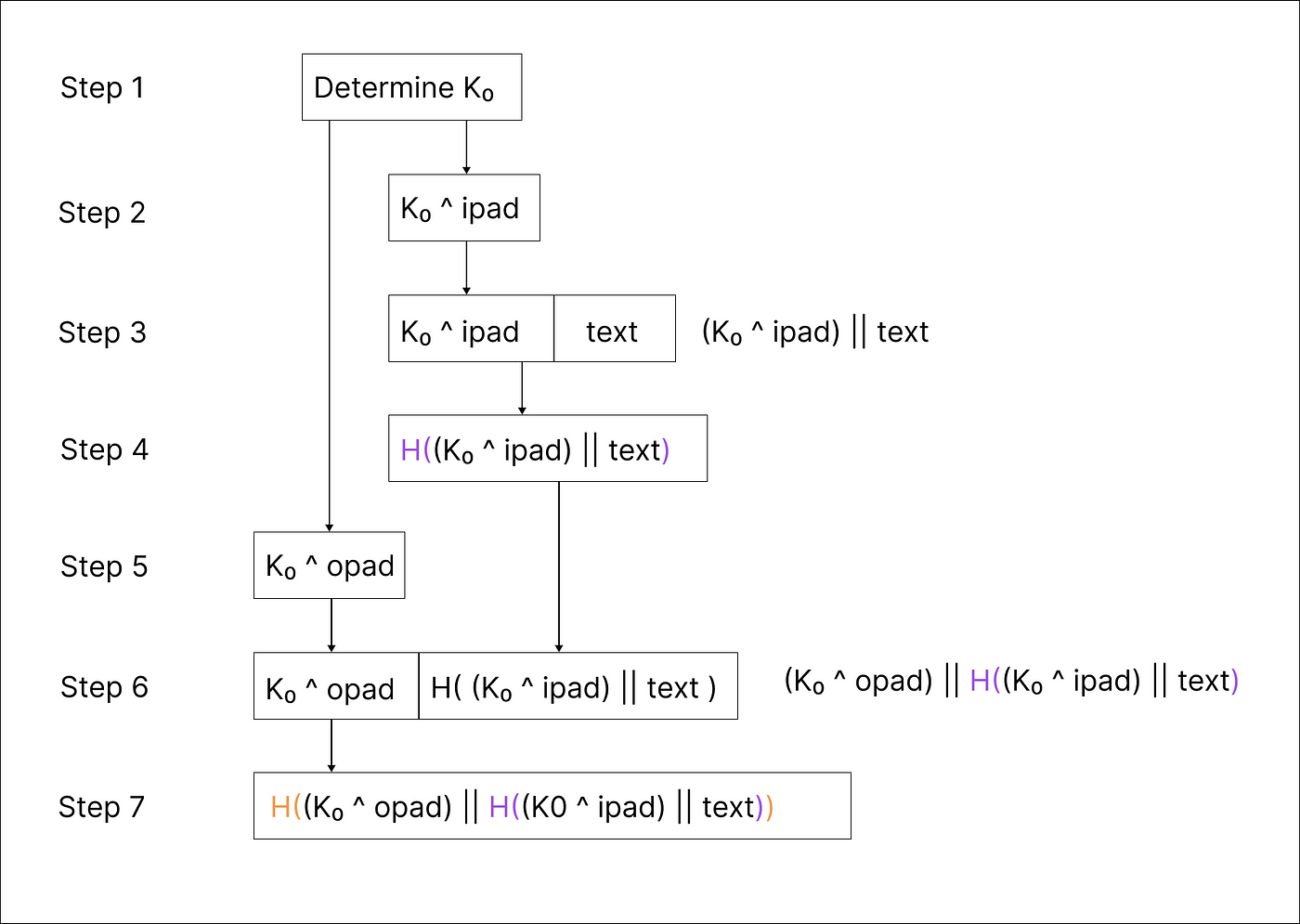

![암호학] HMAC(Hashed MAC) 개념과 과정 암호학] HMAC(Hashed MAC) 개념과 과정](https://blog.kakaocdn.net/dn/1s1Vf/btqEh6BOJV3/Bwk3afhbGhcz4yFKTlWeA0/img.png)